Digital signatures are a cryptographic tool used to verify the authenticity and integrity of digital data.
They are used to confirm that the data originated from a specific sender (authentication) and that it has not been tampered with in transit (integrity).
Here's a simplified explanation of how digital signatures work:
- Key Generation: The sender generates a pair of keys: a private key, which is kept secret, and a public key, which is shared with anyone who needs to verify the sender's signatures.
- Signing: When the sender wants to send a message, they first create a hash of the message. The hash is a fixed-size string of characters unique to the original message. Any change in the message, no matter how small, will result in a completely different hash. The sender then encrypts this hash with their private key. The encrypted hash is the digital signature.
- Verification: Upon receiving the message and the signature, the receiver decrypts the signature using the sender's public key to get the original hash. They then create a new hash of the received message. If the new hash matches the decrypted hash, it proves that the message has not been tampered with and came from the sender.
Digital signatures are widely used in various applications, including email, software distribution, and electronic documents, to ensure data integrity, authentication, and non-repudiation.
Non-repudiation means that the sender cannot deny having sent the message.
Sequence Diagram
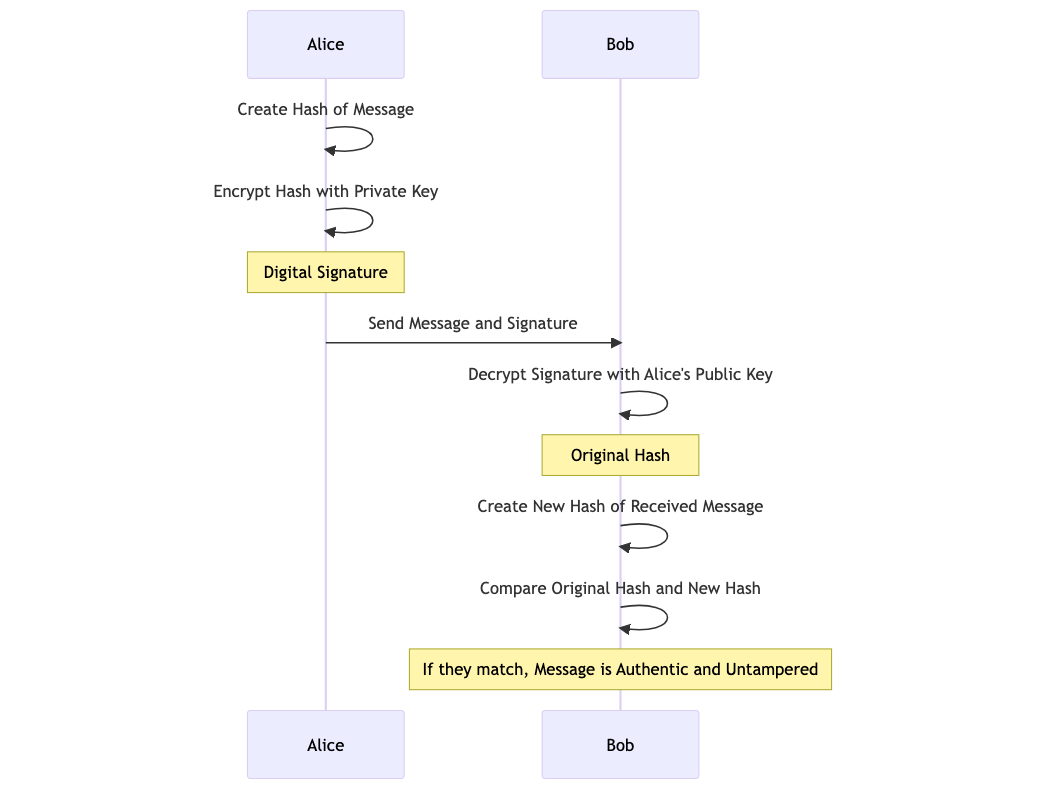
- Alice creates a hash of the message she wants to send.
- She then encrypts this hash with her private key to create the digital signature.
- Alice sends the message and the digital signature to Bob.
- Bob receives the message and the signature. He decrypts the signature using Alice's public key to get the original hash.
- Bob also creates a new hash of the received message.
- He then compares the original hash (from the decrypted signature) and the new hash (from the received message).
- If they match, the message is authentic and has not been tampered with during transmission.
Where do we use it?
Anywhere we have information flowing from outside the trust boundary requires strong integrity and non-repudiation checks.




